Trusted IdPs
In the Federation Authentication Method, RapidIdentity Federation acts as a SAML 2.0 Relying Party to a RapidIdentity Identity Provider or a third-party SAML Identity Provider.
When configuring the Federation Authentication Method for an Authentication Policy, you must choose a previously configured Trusted Identity Provider. Therefore, a Trusted Identity Provider contains all of the configuration necessary to facilitate SAML 2.0 SSO between RapidIdentity Federation and a third-party SAML 2.0 Identity Provider.
SAML 2.0 Trusted IdPs are configured similarly to RapidIdentity Trusted IdPs, but instead of having the fields host and port, they require the fields loginUrl and binding.
Note
If the Trusted IdP is in a domain different from RapidIdentity, you may need to add that domain as an Allowed Origin in the RapidIdentity CORS Security Configuration. The Allowed Origin value should take the form https://trusted_idp_domain.
To add a new IdP, click Add Trusted Identity Provider.
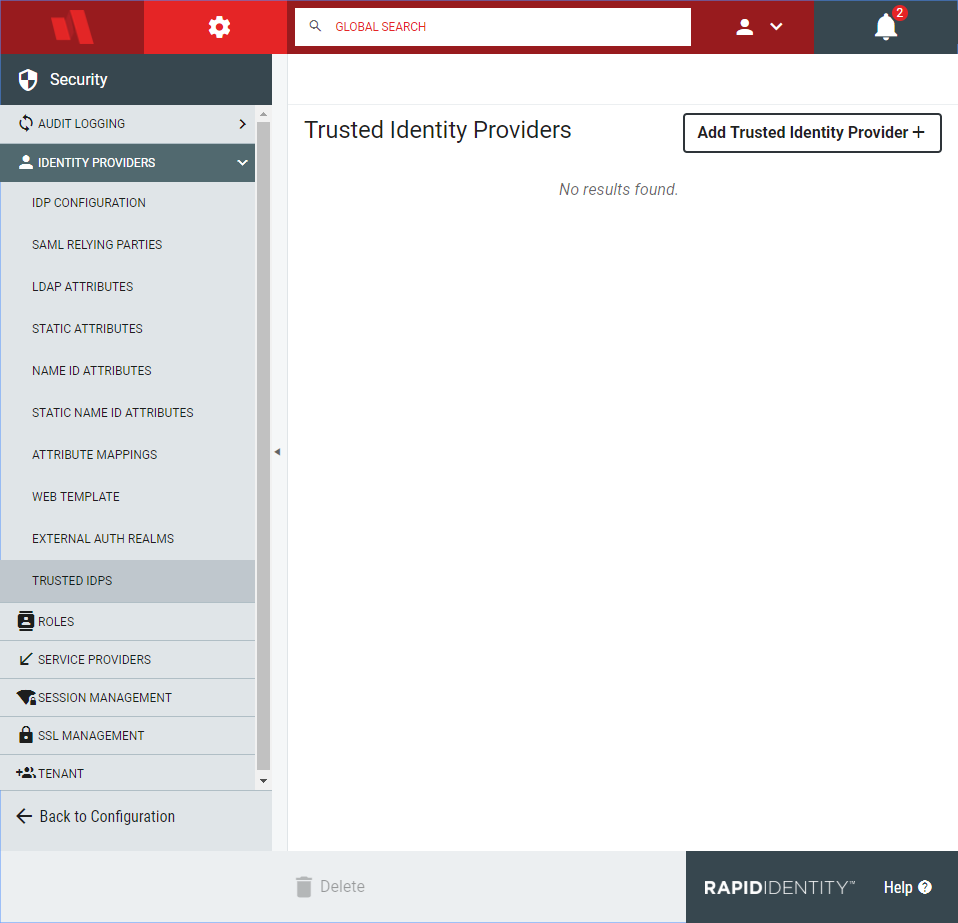 |
A pop-out window will open with form fields. On the General tab, enter the information as provided by the identity provider.
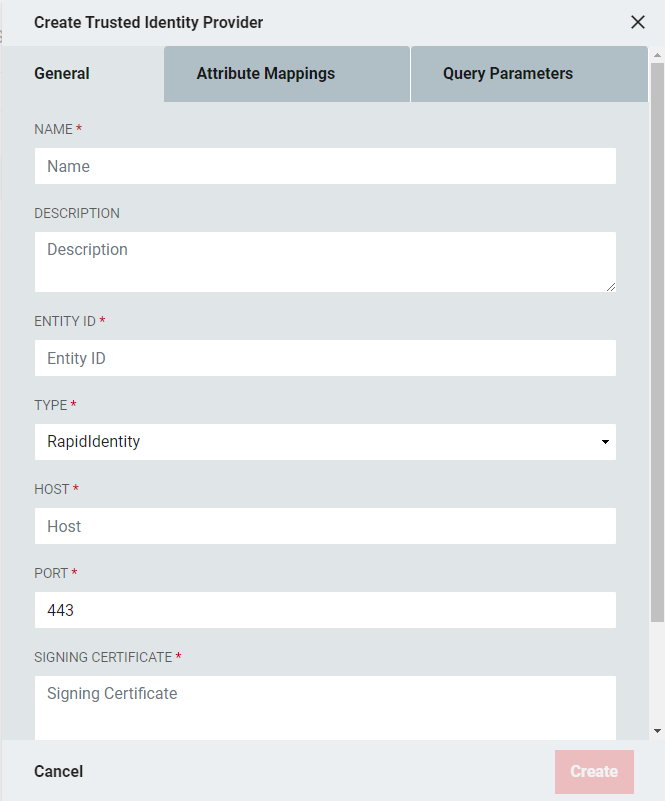 |
Field | Description |
|---|---|
Name | Required field - give the IdP a meaningful name |
Description | Optional description if desired |
Entity ID | The SAML 2.0 Entity ID of the third-party Identity Provider |
Type | The Identity Provider to be used when composing SAML responses. RapidIdentity makes it simple to point to an external RapidIdentity Identity Provider |
*Host | The hostname of the remote RapidIdentity Identity Provider |
*Port | The port the Identity Provider is to use with requests. This defaults to 443 |
Signing Certificate | Cut and paste the provider's certificate into this box |
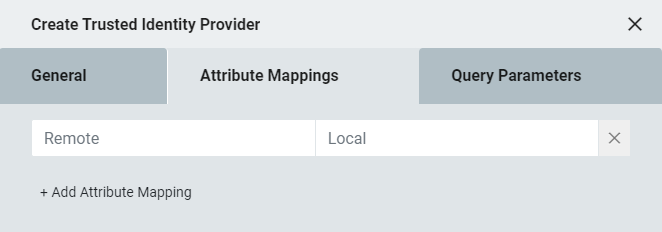
At the bottom of this menu is an option to add Configuration Attribute Mappings. This option allows administrators to map attributes from the local Identity Provider to the remote Identity Provider. To match the same user in both systems, both systems must have a uniquely identifying attribute for each user. For example, if email address is the unique identifier, configure the Local field with the attribute name for email (e.g., "mail"), and the Remote field with the same attribute as it is named in the other system (e.g., "emailAddress").
Note
Attribute Mapping supports a special remote attribute value: @NameID. This indicates that the NameID attribute returned from the Remote Identity Provider should be mapped to the specified Local attribute.
 |